The World Economic Forum’s website has published two great articles by Yuhyun Park, Chair, infollution, ZERO Foundation. The first is about the 8 digital skills we must teach our children. Then a a follow up entitled 8 digital skills children now need and a plan on how to teach them.
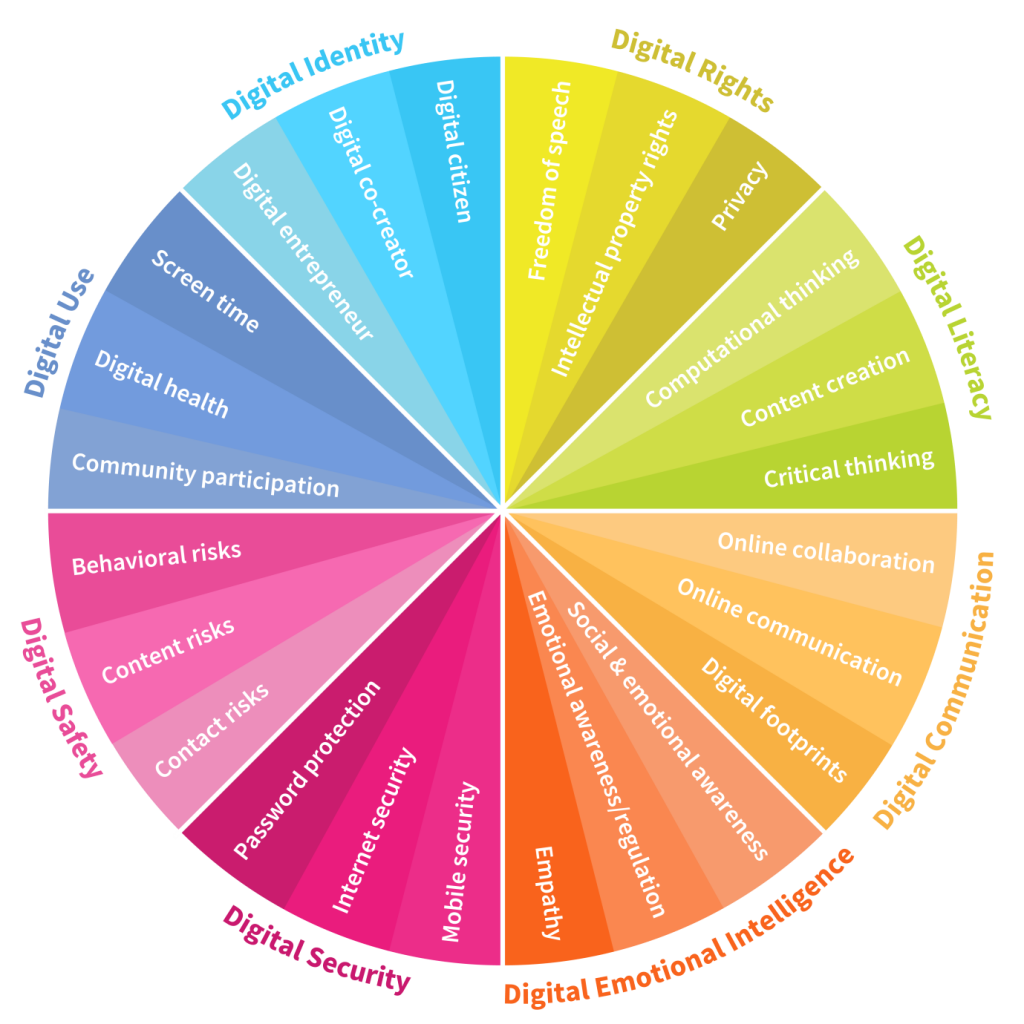
In the first article, Park encourages DQ – digital intelligence [rather than IQ]. DQ is a set of social, emotional and cognitive abilities that enable individuals to face the challenges and adapt to the demands of digital life. These abilities can broadly be broken down into eight interconnected areas:
Digital identity: The ability to create and manage one’s online identity and reputation. This includes an awareness of one’s online persona and management of the short-term and long-term impact of one’s online presence.
Digital use: The ability to use digital devices and media, including the mastery of control in order to achieve a healthy balance between life online and offline.
Digital safety: The ability to manage risks online (e.g. cyberbullying, grooming, radicalization) as well as problematic content (e.g. violence and obscenity), and to avoid and limit these risks.
Digital security: The ability to detect cyber threats (e.g. hacking, scams, malware), to understand best practices and to use suitable security tools for data protection.
Digital emotional intelligence: The ability to be empathetic and build good relationships with others online.
Digital communication: The ability to communicate and collaborate with others using digital technologies and media.
Digital literacy: The ability to find, evaluate, utilize, share and create content as well as competency in computational thinking.
Digital rights: The ability to understand and uphold personal and legal rights, including the rights to privacy, intellectual property, freedom of speech and protection from hate speech.
Without them, the digital divide will continue to be exacerbated. They call it the
The challenge for educators is to move beyond thinking of IT as a tool, or “IT-enabled education platforms”. Instead, they need to think about how to nurture students’ ability and confidence to excel both online and offline in a world where digital media is ubiquitous.
These skills are:
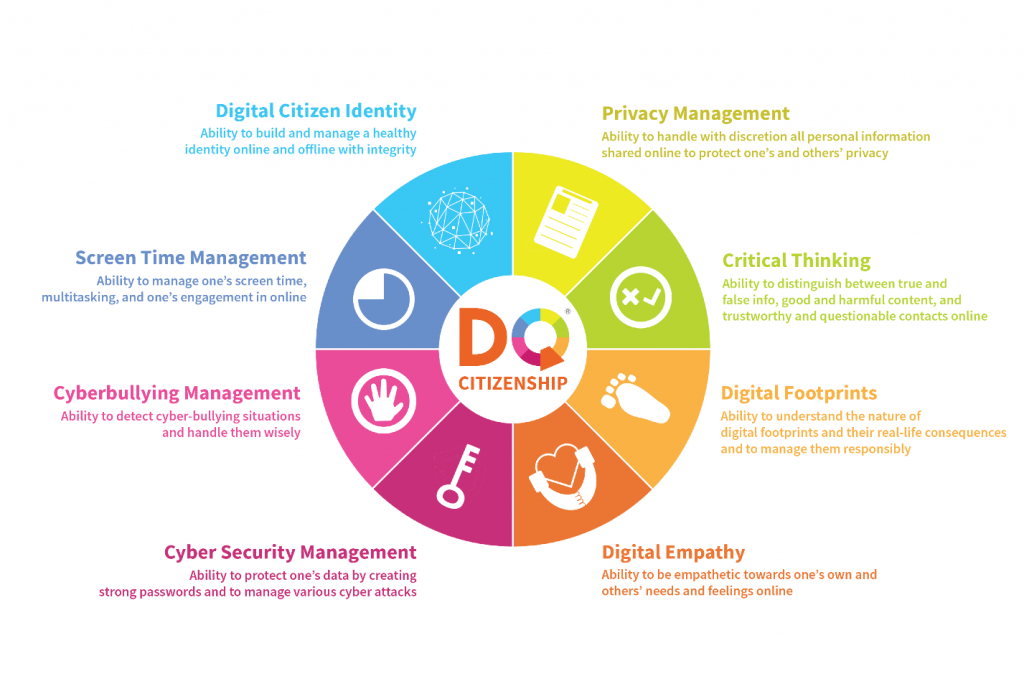
Digital citizen identity: the ability to build and manage a healthy identity online and offline with integrity
Screen time management: the ability to manage one’s screen time, multitasking, and one’s engagement in online games and social media with self-control
Cyberbullying management: the ability to detect situations of cyberbullying and handle them wisely
Cybersecurity management: the ability to protect one’s data by creating strong passwords and to manage various cyberattacks
Privacy management: the ability to handle with discretion all personal information shared online to protect one’s and others’ privacy
Critical thinking: the ability to distinguish between true and false information, good and harmful content, and trustworthy and questionable contacts online
Digital footprints: The ability to understand the nature of digital footprints and their real-life consequences and to manage them responsibly
Digital empathy: the ability to show empathy towards one’s own and others’ needs and feelings online
 Ursula Franklin, in The Real World of Technology wrote:
Ursula Franklin, in The Real World of Technology wrote: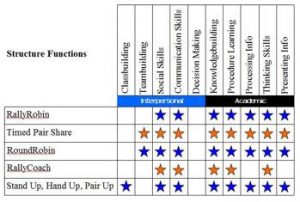 How can we engage students in our classes? There are many great articles on the web on this topic, and perhaps one of the most prominent are the Kagan structures:
How can we engage students in our classes? There are many great articles on the web on this topic, and perhaps one of the most prominent are the Kagan structures:  In this day and age, privacy has never been more important. There are many privacy tools online from respected organizations, first and foremost among them is EFF – the Electronic Frontier Foundation. I personally use their
In this day and age, privacy has never been more important. There are many privacy tools online from respected organizations, first and foremost among them is EFF – the Electronic Frontier Foundation. I personally use their 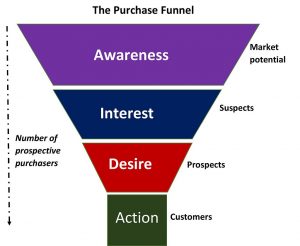 According to Wikipedia, AIDA is an acronym that stands for Awareness, Interest, Desire and Action. The AIDA model is widely used in marketing and advertising to describe the steps or stages that occur when a consumer engages with an advertisement or other type of marketing communication. The AIDA model proposes that advertising messages need to accomplish a number of tasks in order to move the consumer through a series of sequential steps from brand awareness through to action (purchase and consumption). The AIDA model is one of the longest serving models used in advertising, having been developed in the late nineteenth century.
According to Wikipedia, AIDA is an acronym that stands for Awareness, Interest, Desire and Action. The AIDA model is widely used in marketing and advertising to describe the steps or stages that occur when a consumer engages with an advertisement or other type of marketing communication. The AIDA model proposes that advertising messages need to accomplish a number of tasks in order to move the consumer through a series of sequential steps from brand awareness through to action (purchase and consumption). The AIDA model is one of the longest serving models used in advertising, having been developed in the late nineteenth century.